AI’s phishing influence – ‘we’re already seeing it’

AI’s phishing influence – ‘we’re already seeing it’ | Insurance Business America
Cyber
AI’s phishing influence – ‘we’re already seeing it’
Insurance expert and ex-FBI special agent on scams and their emotional impact
The influence of generative AI is already being seen in phishing attempts, a cybersecurity expert at brokerage Hub International (HUB) has told Insurance Business.
“We’re already seeing it,” Brian Schnese (pictured below), Hub senior risk consultant, said. “It used to be that you could spot a phishing email by a few characteristics – ‘oh, that’s not proper English, or there’s something culturally off with the message that they’re sending, or … [the spelling] isn’t quite right’, there were clues.
“We’re in a world today where I can go to ChatGPT and type in, ‘please craft a request to my vendor asking them to change my wiring instructions’, and it spits out a perfect request. [I can then go] back to ChatGPT and say, ‘please add a sense of urgency and stress the confidential nature of this transaction’ –and again, instantly, it’s perfect.”

Schnese, a former FBI special agent who has worked closely with the Royal Canadian Mounted Police, sat down with Insurance Business at RIMS Canada 2023 to discuss the growing business email compromise threat, why spear phishing poses a big risk to organizations today, and the emotional toll that falling victim to a scam can take.
Spear phishing – how fraudsters are crafting the “perfect” scam attempt
Most workers have, by now, probably seen a suspicious email in their inbox, perhaps requesting an update to stored bank details or requesting a payment. These attempts to mine information and credentials from unwitting staff for financial gain are known as phishing, and many use social engineering techniques to try to trick others into lining their pocket, with many individuals often receiving the same email.
Spear phishing, as Schnese describes it, is a step up from these attempts to throw emails at the wall and see what sticks.
“It is different than just phishing, phishing being a non-tailored attempt at getting you to click on something and spearfishing being something that is crafted just for you,” Schnese said. “They know about you, they know about the conversation you’ve been having with your vendor or with your director, and so they’re crafting a perfect attempt at a scam.”
Typically, spear phishing fraudsters will try to sniff out the “perfect victims”, which could include executives and senior leaders, as well as senior finance officers and individuals in accounts payable. Spear phishers might impersonate a vendor, or they might masquerade as an internal executive.
Spear phishing attacks could be even more prevalent than first thought
With limited sources for information on spear phishing attacks outside of insurance companies and law enforcement, the scale of the problem remains cloaked in uncertainty.
“We just don’t have 100% visibility,” Schnese said.
Insurance data suggests that business email compromise is a more common problem than ransomware, though it is typically less costly. Corvus Insurance, which regularly publishes cyber threat reports, revealed in its Q4 2022 cyber risk insights index that fraudulent funds transfers made up nearly 28% of its all-time claims, while ransomware category incidents stood at 23%.
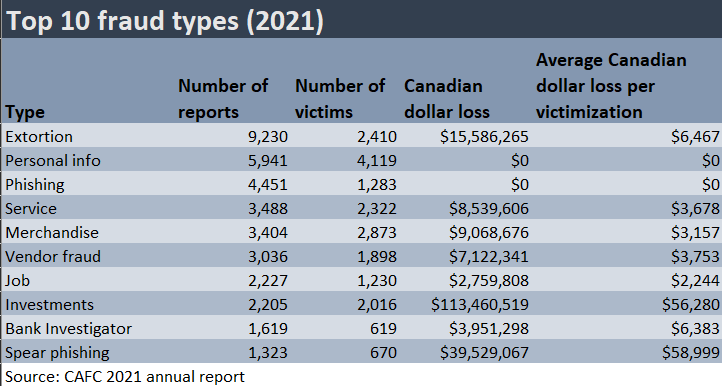
In 2021, 1,323 reports of spear phishing were made to the Canadian Anti-Fraud Centre (CAFC), equivalent to a Canadian dollar loss of more than CA$39.5 million ($29.2 million). On average, the loss per victim was CA$58,999.
However, Schnese speculated that this figure likely does not paint a full picture, because the CAFC estimates that just 5% to 10% of fraud connected to Canadian victims gets reported to it.
In July, the US SEC brought in rules that force companies to disclose material cybersecurity incidents and breaches, meaning the picture on at least one side of the border is likely to become clearer.
In the case of spear phishing, embarrassment at having fallen for a scam and a wish to avoid “airing dirty laundry”, in Schnese’s words, could have put businesses off reporting prior to regulatory changes.
The emotional toll of falling victim to spear phishing attacks
A scam’s impact may not just be financial, and affected individuals can face a mental toll.
In 2019, Ottawa’s city treasurer Marian Simulik was tricked into wiring more than $97,000 to a scammer after receiving fake emails from someone who purported to be the city manager.
The fraud was discovered when the fake city manager tried to convince Simulik to make a second transfer. The city treasurer saw the email while in the same room as the real city manager, and approached him in person, exposing the fraud.
“I just thought her emotional statements were really impactful, because this is gross, and it gets so tailored, and it’s so specific, and it’s so difficult,” Schnese told Insurance Business. “And then the fallout is, yes, loss of funds, but it’s total shame and embarrassment – so those are the stakes, and that’s what you have to lose.”
Related Stories
Keep up with the latest news and events
Join our mailing list, it’s free!






