Australia among top countries affected by ransomware attacks

The Bitdefender Threat Debrief (BDTD) is a monthly series analysing threat news, trends, and research from the previous month. The latest report reveals the countries most affected by ransomware attacks, the top ransomware families detected, and the top trojans targeting Android in October 2022.
Top 10 countries most affected by ransomware attacks in October 2022
Bitdefender detected ransomware from 150 countries in its latest dataset, proving that ransomware continues to be a threat that touches almost the entire world. As shown above, Australia took the eighth place, while the United States (US), Brazil, and Iran were the top three, accounting for a collective 52%.
“Many ransomware attacks continue to be opportunistic, and the size of population is correlated to the number of detections,” the report said.
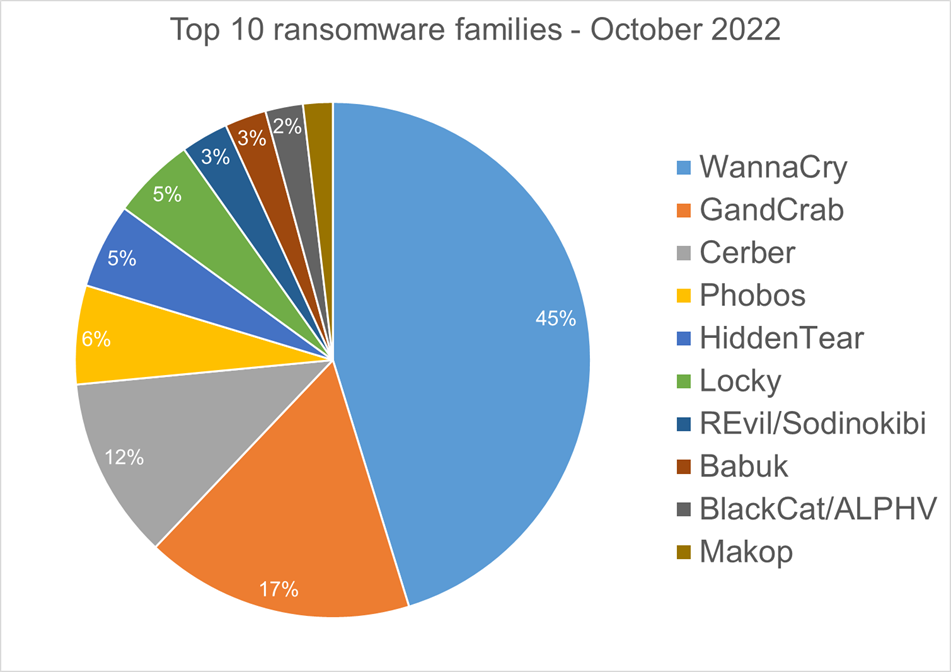
Top 10 ransomware families in October 2022
After analysing malware detections from October 1 to 30, Bitdefender identified 189 ransomware families. The number of detected ransomware families may vary each month, depending on the current ransomware campaigns in different countries. In October, WannaCry, GandCrab, and Cerber were the top ransomware families detected, accounting for 74% collectively, with REvil/Sodinokibi also making an appearance.
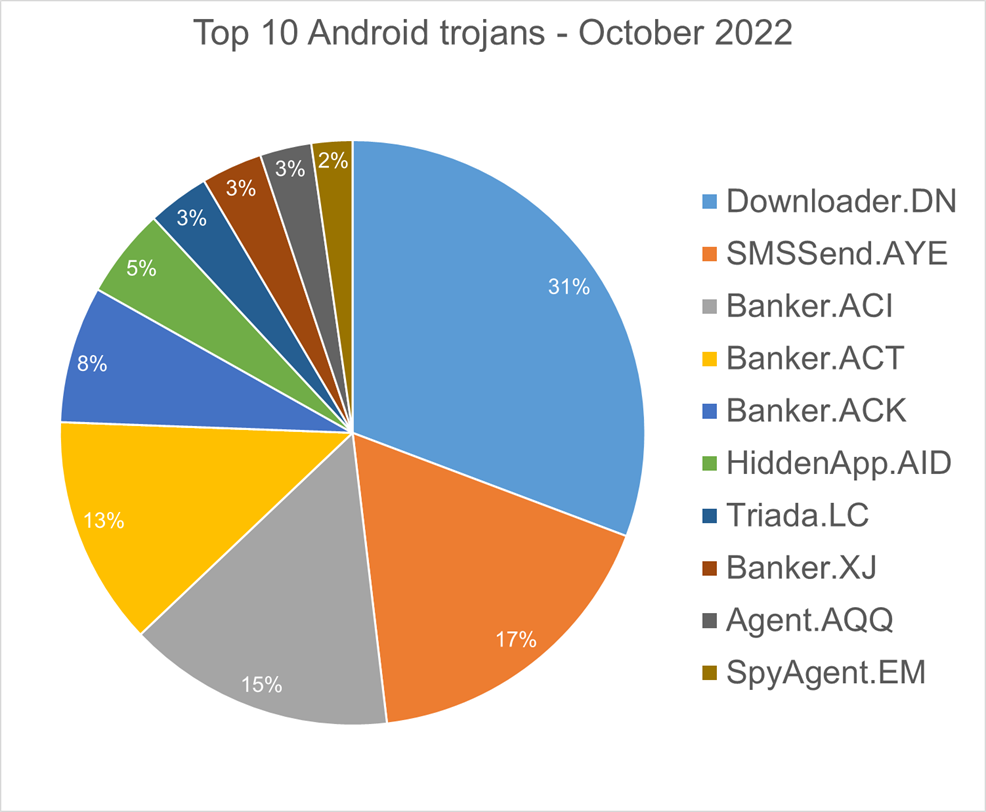
Top trojans targeting Android in October 2022
According to Bitdefender’s telemetry in October 2022, the top trojans targeting Android during the month were:
Downloader.DN – Repacked applications from Google App Store and bundled them with aggressive adware. Some adware downloads other malware variants.
SMSSend.AYE – Malware that tries to register as the default SMS application on the first run by requesting the user’s consent. If successful, it collects the user’s incoming and outgoing messages and forwards them to a Command & Control (C&C) server;
Banker.ACI, ACT, ACK – Polymorphic applications that impersonate legit apps (e.g., Google, Facebook, and Sagawa Express). Once installed, it locates banking applications on the device and tries downloading a trojanised version from the C&C server;
HiddenApp.AID – Aggressive adware that impersonates AdBlock applications. When running for the first time, it asks permission to display on top of other apps. With this permission, the application can hide from the launcher;
Triada.LC – Malware that gathers sensitive information about a device (e.g., device IDs, subscriber IDs, and MAC addresses) and sends them to a malicious C&C server. The C&C server responds by sending back a link to a payload which the malware downloads and executes;
Banker.XJ – Applications that drop and install encrypted modules. This trojan grants device admin privileges and gains access to manage phone calls and text messages. After deploying, it maintains a connection with the C&C server to receive command and upload sensitive information;
Agent.AQQ – A dropper malware is a trojan that hides the dangerous payload inside an app as an evasion technique. If it can avoid security defences, this payload is deployed. The malicious payload is decrypted and loaded by the dropper; and
SpyAgent.EM – Applications that exfiltrate sensitive data like SMS messages, call logs, contacts, or GPS location.
Lockton’s latest research found that technology and cybersecurity were the top risks facing chief financial officers (CFOs) during Q1 and Q3 2022. Meanwhile, security giant Sophos’ 2023 Threat Report advised organisations to brace themselves for a hostile cyber environment in 2023.





